Role-Based Access Control
Deeper DiveFor more in-depth information, check out our detailed documentation on the following topics:
Role-Based Access Control
Need any help?If something in this tutorial isn't working as expected, feel free to contact our support team via Slack.
Below is a text-only guide for users based on the above video
What is an Access Role?
Access roles give companies the ability to limit human or machine access rights and Akeyless offers a very powerful and granular role-based access control system that follows least privileged access principles. You can associate authentication methods with Access roles. You can create as many roles as you want and each of them has their own set of permissions.
There are also Sub-claims, which are policies for authentication methods, that can be defined within a role that gives specific groups or users within those groups authorization to use that role. Sub-claims can be something like a group name and email address to limit access to a specific user or some other identifier that gives access to any number of users, or specific user, for the given authentication method. Sub-claims are added when an authentication method is associated with an access role.
Create an Access Role via the UI
Choose the Access Roles option from the left-side menu.
Click ‘New’, choose the name for your role, and click 'Next.
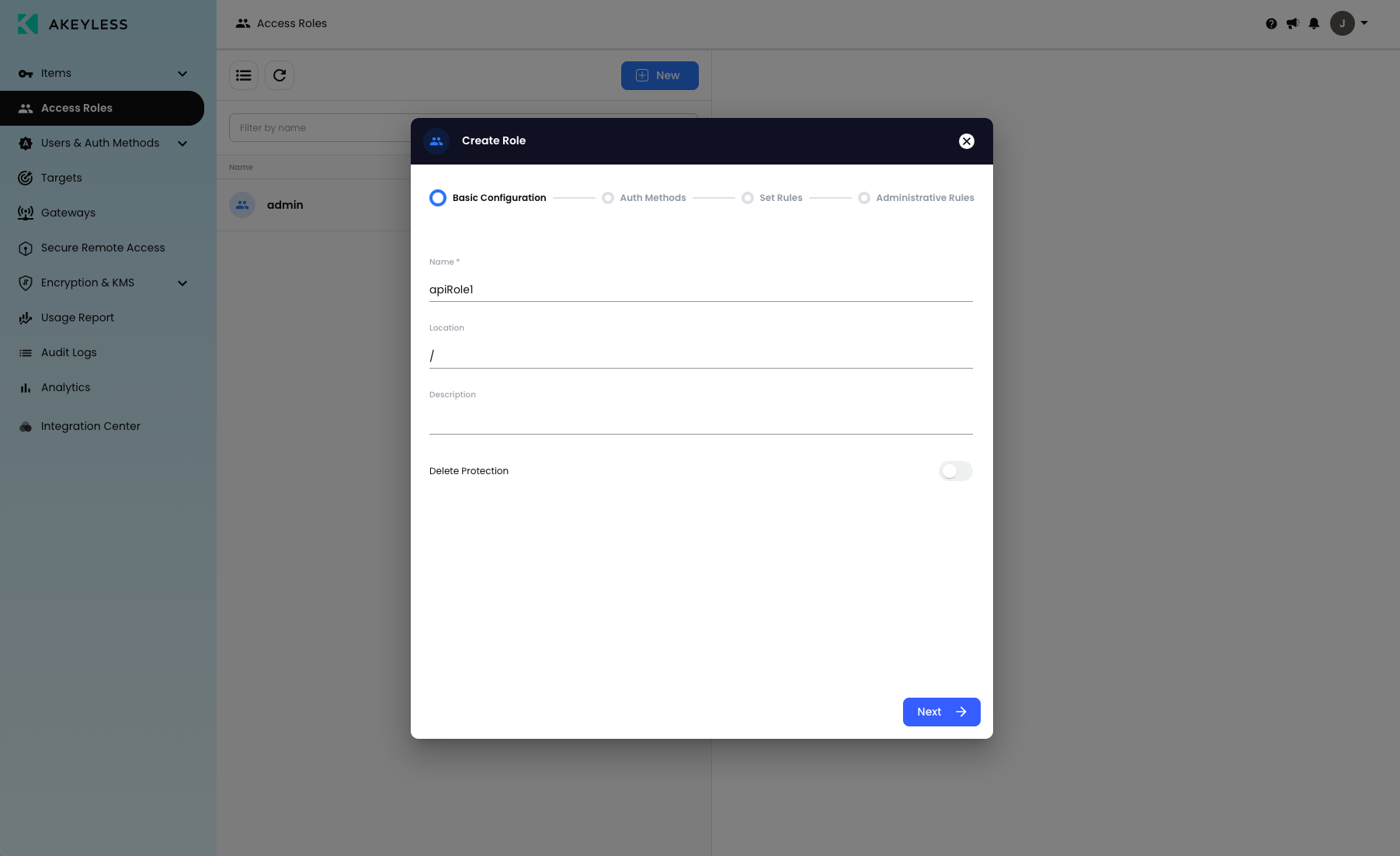
Click the ‘Associate’ button on the right-hand side of the popup and choose the auth method to associate, then click ‘Save’ and 'Next'.
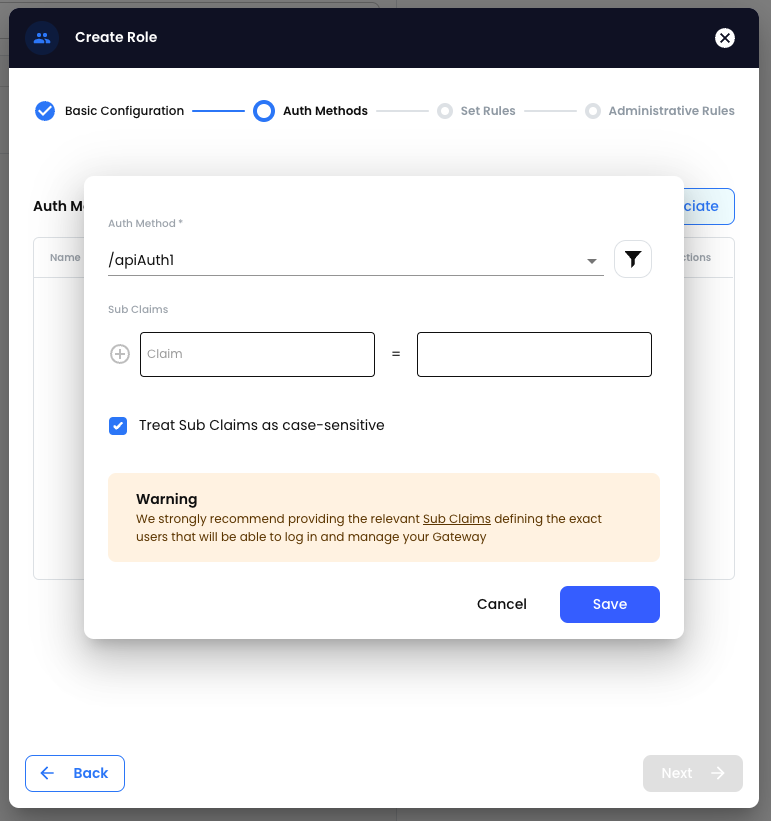
Click the ‘Add’ button on the right-hand side of the popup, select the 'Type' of resource including 'Path' and 'Permissions' for the role. Then click 'Save' and 'Next'.
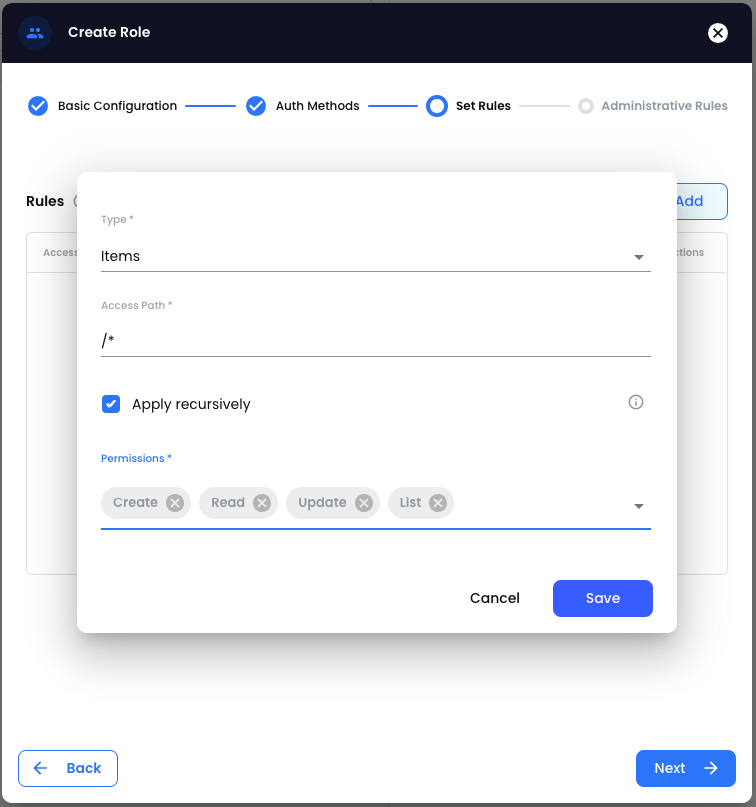
To use the Authentication Method and Access Role, the user given the Access Key and Access ID should log into their account as follows.
Go to console.akeyless.io.
Click the ‘Access Key’ image under the ‘Sign in’ button.
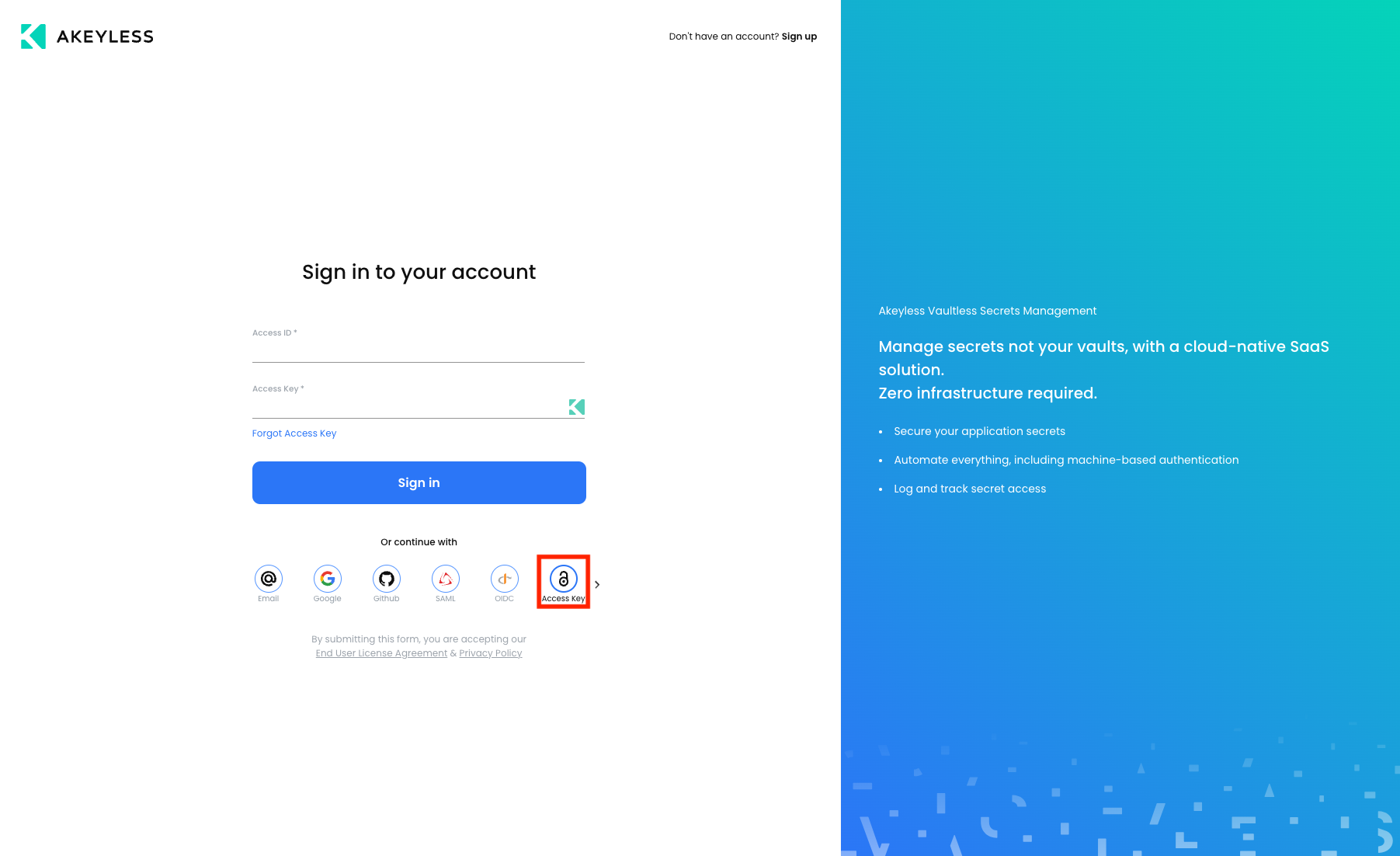
Use the Access ID and Access key given and choose ‘Sign In’
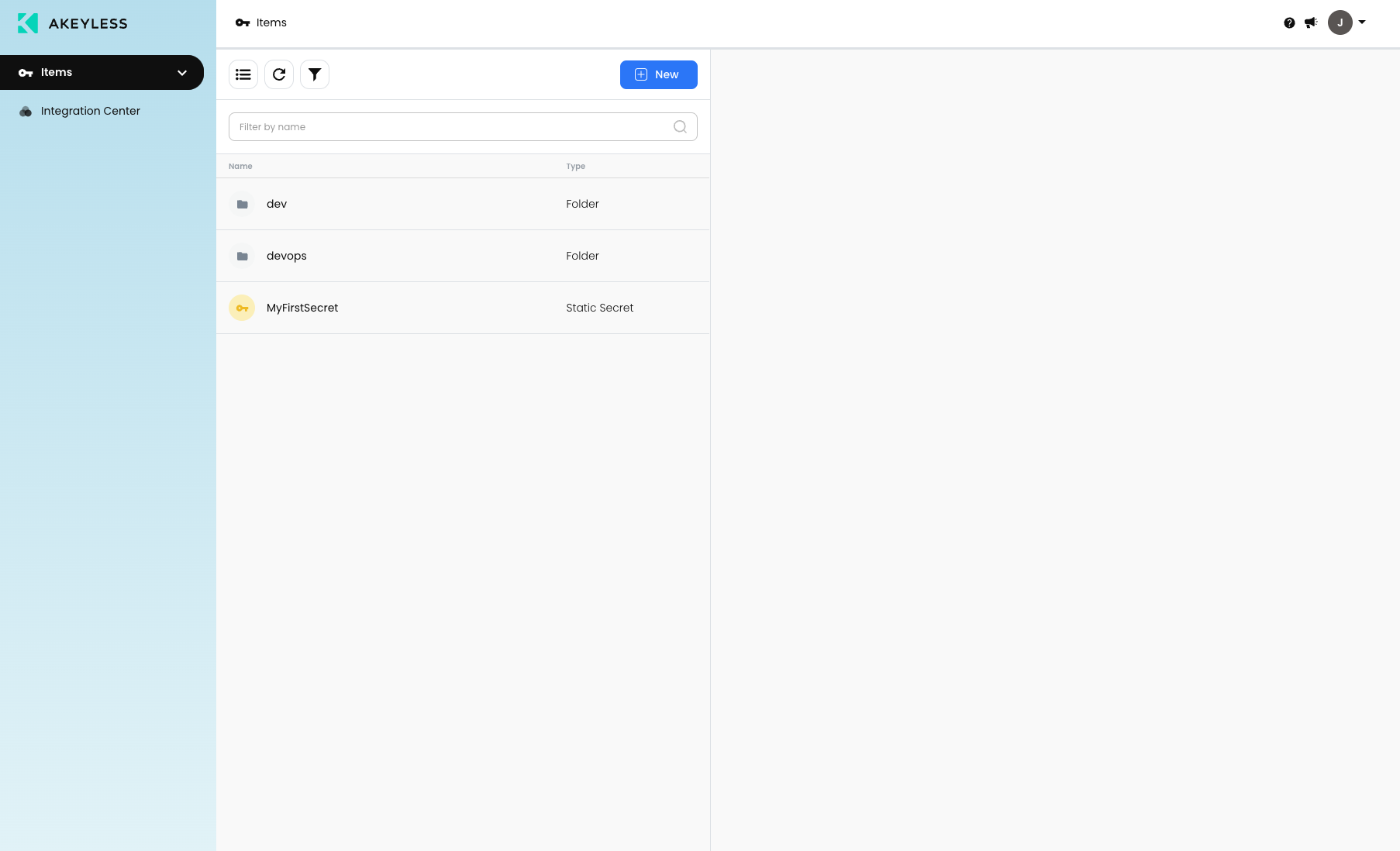
Once logged in, the user will see only what they have been given access to and will only be able to work based on permissions given.
Create an Access Role via the CLI
The same process can be done via Akeyless CLI using the below commands (with variations depending on permissions).
This is the order of commands:
- Create a role
akeyless create-role --name [role_name]- Associate an Authentication Method
akeyless set-role-rule --role-name [role_name] --path "/path/to/folder/*" --capability read --capability create --capability update- Set permissions
akeyless assoc-role-am --role-name [role_name] --am-name [authentication_method_name]Updated about 1 year ago
