Creating and Using a Tokenizer
Deeper DiveFor more in-depth information, check out our detailed documentation on the following topics:
Tokenization
Need any help?If something in this tutorial isn't working as expected, feel free to contact our support team via Slack.
Below is a text-only guide for users based on the above video
What is Tokenization?
Akeyless offers tokenization-as-a-service. Tokenization is the process of encrypting sensitive data such as a social security number, phone number, or credit card number in a way that preserves the data format and uniqueness, and allows for data encryption at a later time as well.
For example, you would encrypt a 16-digit credit card number so that the ciphertext is another 16-digit number. It's important to preserve the data format for two reasons:
- The data needs to still pass certain validation checks of which the format is one, so companies can use this method to avoid costly and time consuming changes to data models and code.
- Keeping this format means that data such as credit cards or social security numbers can still be used as a unique key to identify a row in a database.
Akeyless supports vault-less tokenization, meaning that a tokenized secret is not stored in Akeyless at any time during or after the tokenization process and we provide built-in tokenization templates for credit, debit, and prepaid cards, social security numbers, U.S phone numbers, as well as a custom tokenization template option.
Creating a Tokenizer
You can create a Tokenizer through the UI or the CLI.
Creating a Tokenizer through the UI
Click 'New' -> 'Tokenizer' and choose the Name and Tweak Type. For this example, we are using the Internal option. Check the Tokenization docs to see what each type does.
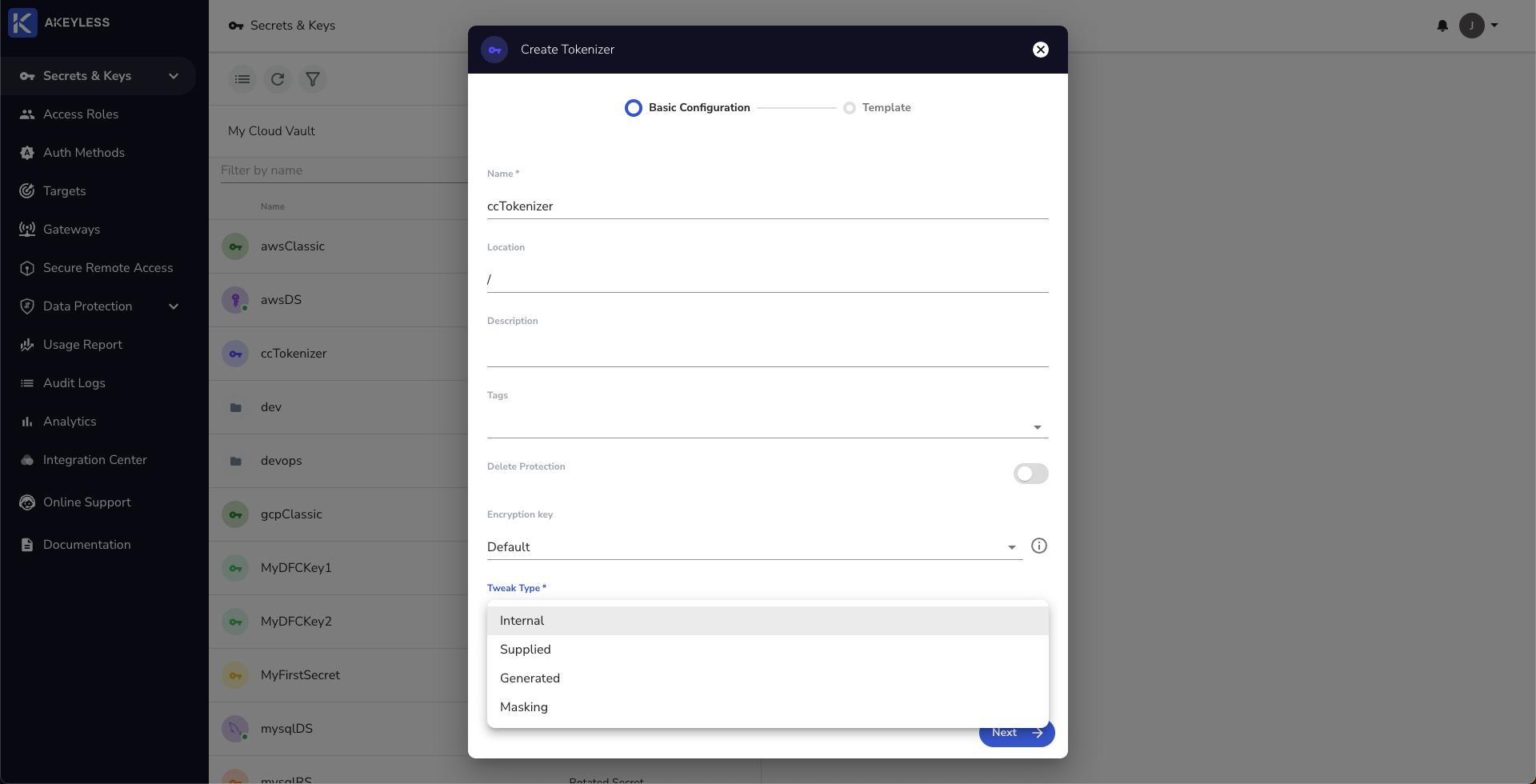
Next, choose your Template or Custom. In this example, we will use the Credit Card option.
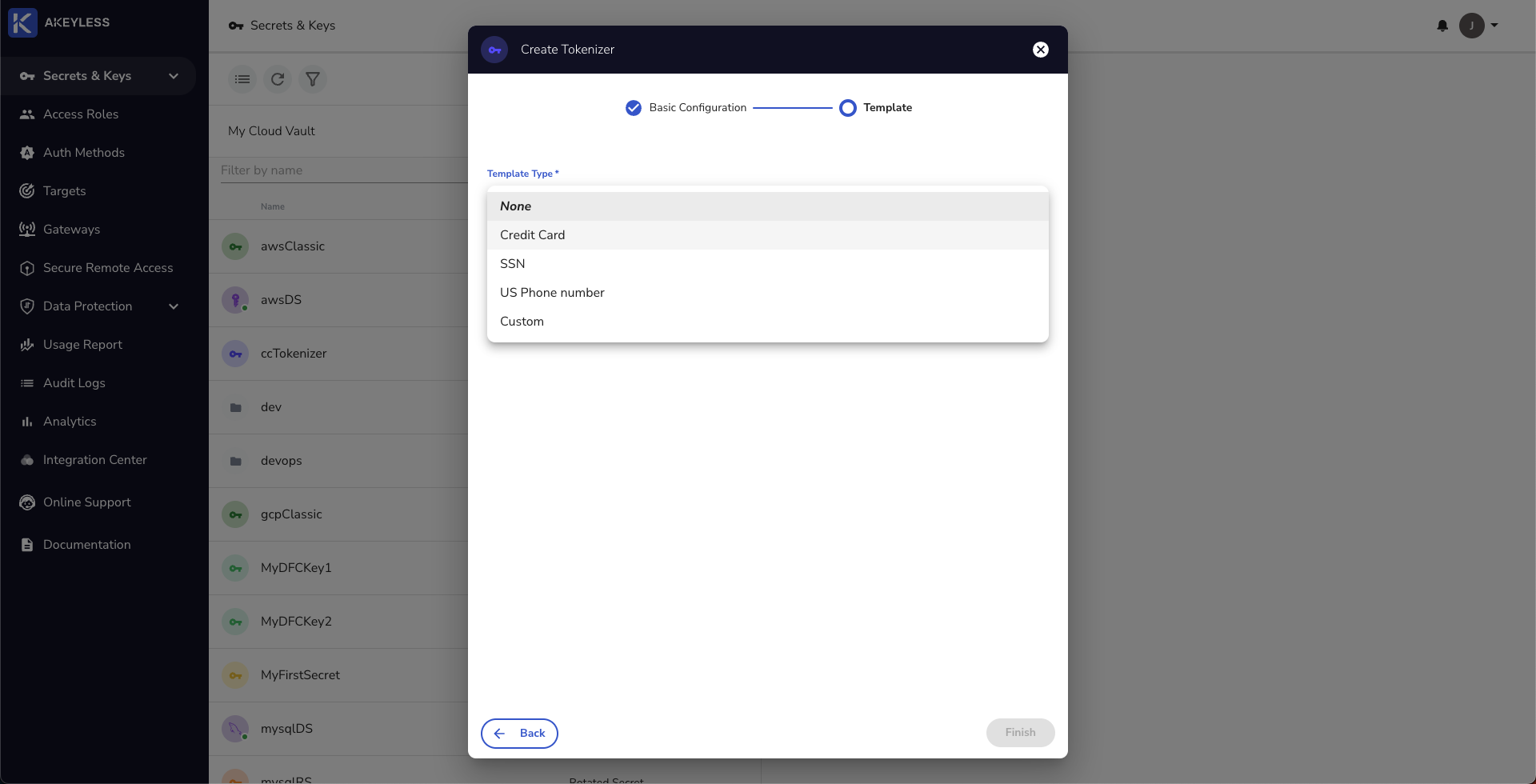
Creating a Tokenizer from the CLI
Us the following command to create the Tokenizer.
NoteCustom tokenization has additional mandatory parameters. Also, Akeyless currently supports vaultless tokenization only and the default value of this parameter is vaultless.
akeyless create-tokenizer \
--name <Tokenizer name> \
--tokenizer-type <vaultless> \
--template-type <SSN, CreditCard, USPhoneNumber> \
--tweak-type <Supplied, Generated, Internal, Masking>Tokenize and Detokenize a Secret
Once we have our token ready, we can go ahead and use it to tokenize and detokenize data from the UI or CLI.
Tokenize and Detokenize a Secret from the UI
Click the Tokenize/Detokenize button and add your plaintext credit card number. The credit card number must be Luhn compliant and you need to add dashes for this to work.
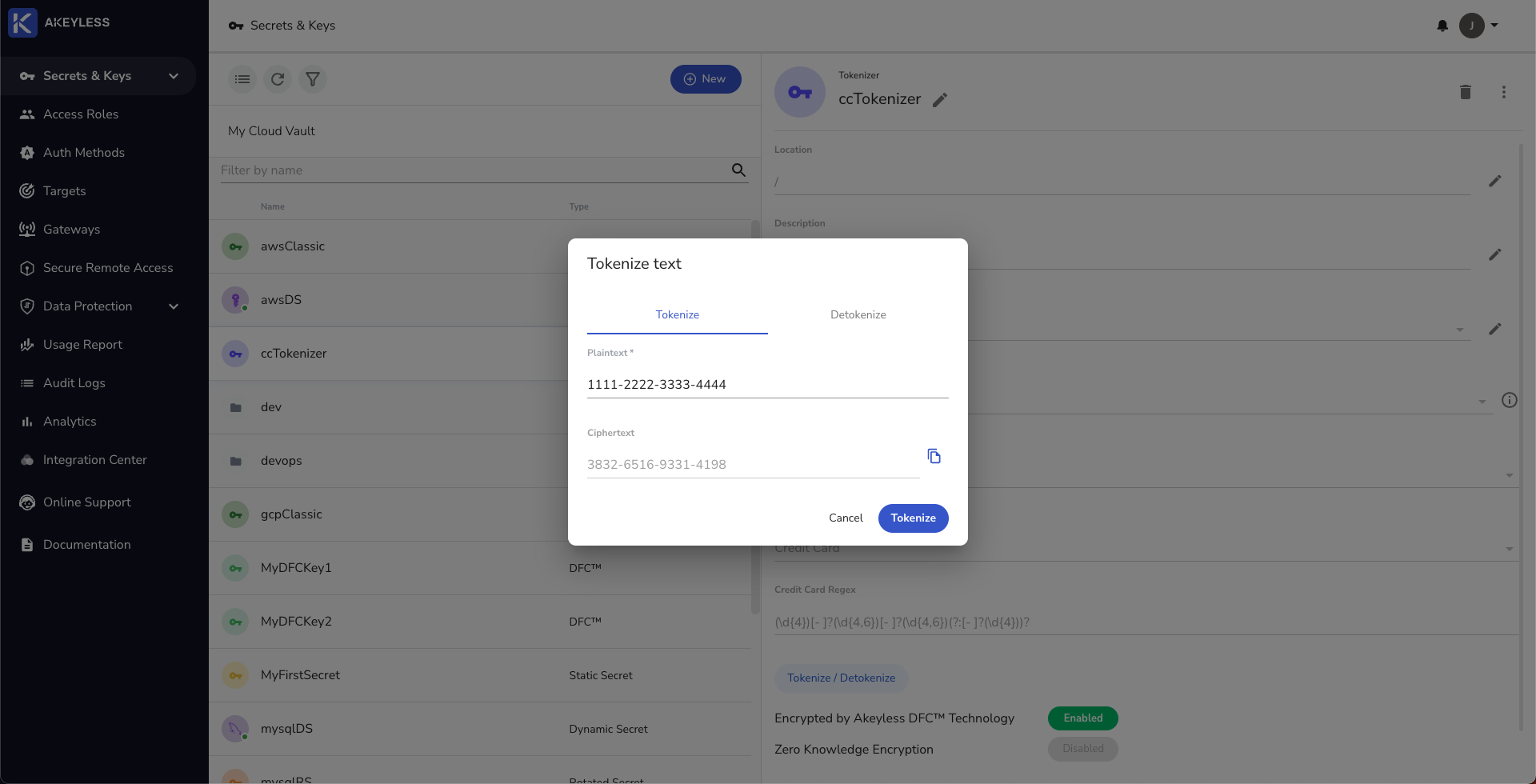
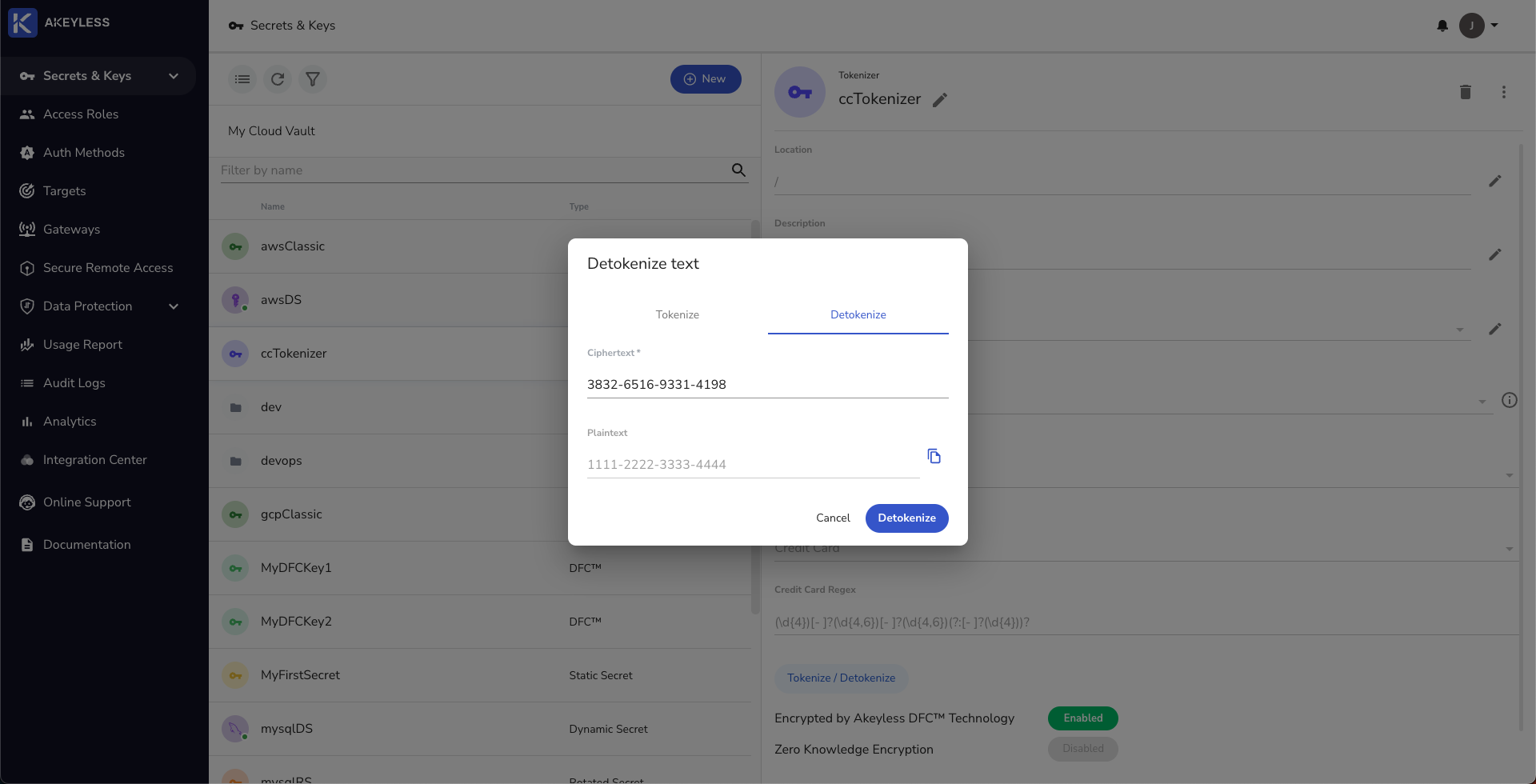
With the encoded text, we can now detokenize it using the same method just by clicking on the Detokenize tab and enter the encoded text to get the plaintext.
Tokenize and Detokenize a Secret from the CLI
To Tokenize a secret from the CLI, run the following command.
akeyless tokenize \
--tokenizer-name <Tokenizer name> \
--plaintext <Data to be encrypted> \
--tweak <Base64-encoded tweak value>To Detokenize a secret from the CLI, run the following command.
akeyless detokenize \
--tokenizer-name <Tokenizer name> \
--ciphertext <Data to be decrypted> \
--tweak <Base64-encoded tweak value that was used for encryption>Updated about 1 year ago
