Kubernetes Secrets Migration Into Akeyless
Deeper DiveFor more in-depth information, check out our detailed documentation on the following topics:
Automated Kubernetes Secrets Migration
Need any help?If something in this tutorial isn't working as expected, feel free to contact our support team via Slack.
Below is a text-only guide for users based on the above video
Why Migrate Your Secrets to Akeyless?
When you become an Akeyless user, it is a good idea to ensure all of your secrets are located inside the platform so there are fewer leaks. It also helps that all of your secrets are secured by Akeyless' patented DFC cryptography.
Prerequisites
Notes
- Akeyless currently only has static secret migration capabilities.
- If there are existing secrets under the Target location, their values will be replaced in case of conflict. This can happen if you leave the "Target location" field blank and a new secret has the same name as the existing one.
TipBefore getting started, ensure that the platform where the secrets are stored is accessible over the network from the Akeyless Gateway server. Depending on the deployment, it might require adding an Akeyless Gateway IP address to a security group or a firewall.
Akeyless supports secrets migration from Kubernetes Secrets using Kubernetes API.
Three types of authentication are available:
- Bearer Token
- Certificate
- Password
In this demo, we will use the Bearer Token option. And to get this done, you will need the following details for your Kubernetes cluster:
- Cluster Endpoint URL
- Cluster CA Certificate
- Bearer Token
Migrating Secrets from Kubernetes into Akeyless
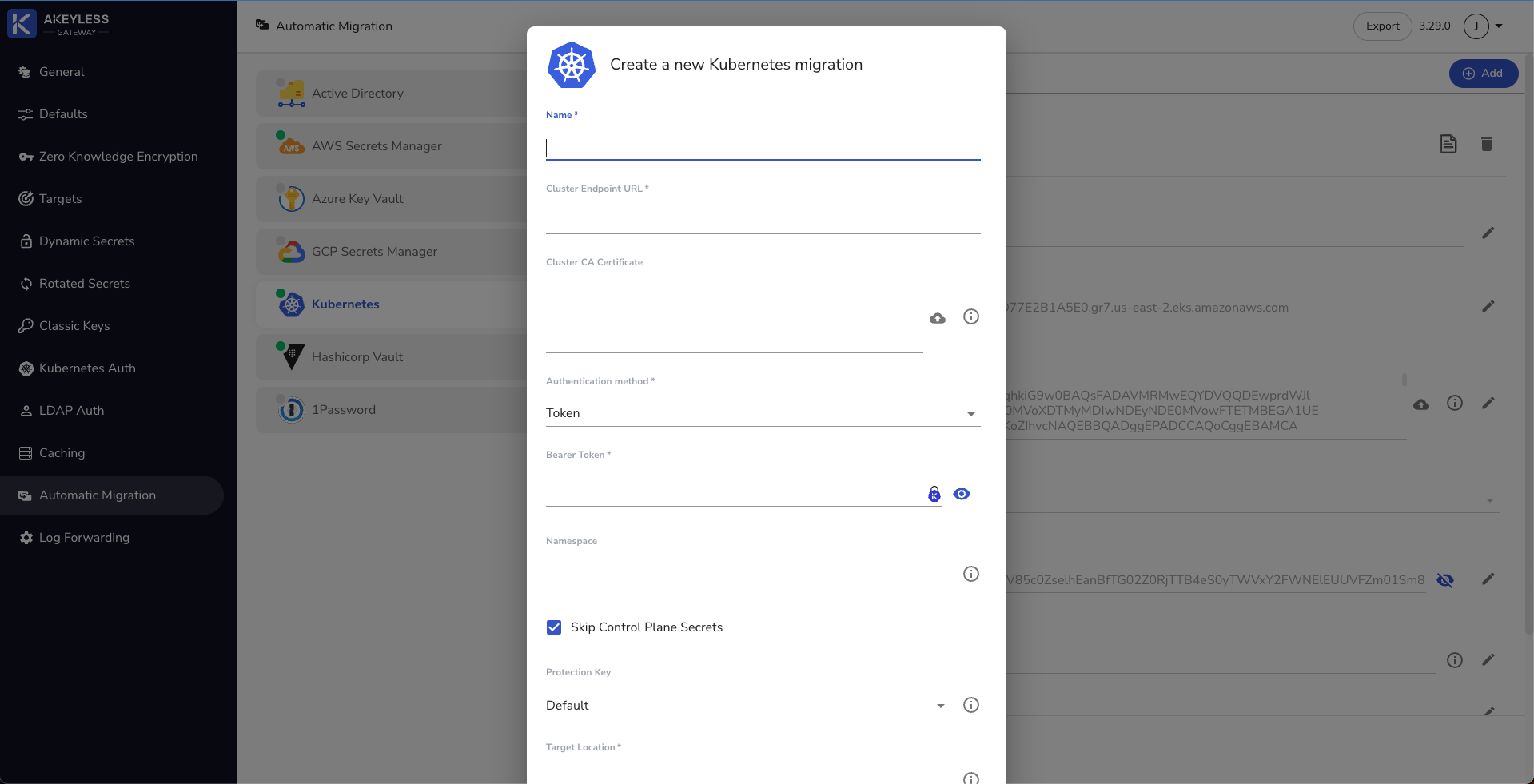
Log into your Gateway console and click on Automatic Migration -> Kubernetes.
Enter the details of you cluster and click Save. Then click on the Sync Now button and all of your static secrets from Kubernetes will show up in the folder you chose.
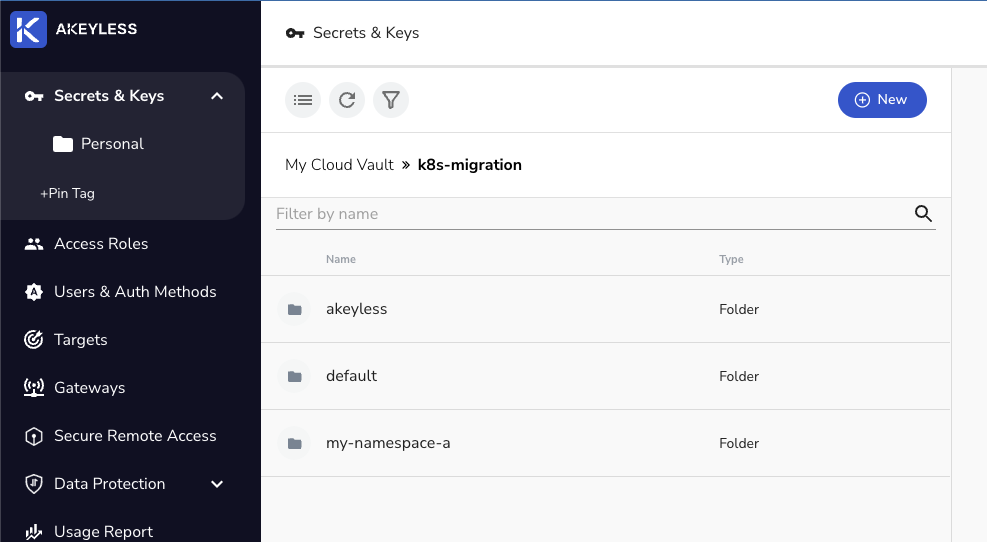
Head back to your Akeyless Console and you will see your secrets in the folder.
Updated about 1 year ago
